NIST ZTA Guide Highlights the Need for Identity Correlation
- Lauren Selby
- July 19, 2022
- Cybersecurity
- 6 MIN READ
How To Build the Foundation for Zero Trust
A new report underlines the critical importance of identity integration for cybersecurity initiatives—specifically, the emergent standard of Zero Trust Architecture (ZTA).
In this post, we’ll be further exploring a topic we’ve discussed many times: the centrality of identity unification and correlation to the organization’s overall security architecture—as highlighted by the role Radiant Logic plays in the new ZTA guide.
The National Cybersecurity Center of Excellence (NCCoE), a part of the National Institute of Standards and Technology (NIST) has assembled a lab to define best practices for implementing Zero Trust with solutions already available on the market or potentially already deployed at your organization. The resulting 100+ page Cybersecurity Practice Guide provides a complete example of ZTA to guide implementation. TL;DR? Check out our summary here.
Who’s Afraid of Zero Trust?
The open “secret” in our market is that identity data management continues to be a major roadblock to many organizations’ top priority projects: digital transformation, improved customer experience, less-headachy compliance to regulations, rock-solid security; all are stymied by a lack of cohesive, organization-wide strategy around identity data.
NIST recognizes this challenge in their guide: “Enterprises that want to migrate gradually to an increasing use of ZTA concepts and principles in their network environments will need to integrate ZTA with their legacy enterprise and cloud systems.” (lines 479-481). Cool, but how?
Organizations often have a variety of data sources housing identity information (aka, identity sprawl). These identity data sources include directories, often multiple Active Directory domains and forests as well as legacy LDAP directories, relational databases like Microsoft SQL Server and Oracle, even ultra-legacy sources like mainframes… and more. This is one source of complexity for the enterprise to manage: not only do the types of data sources vary, each represents identities differently. There are different access points, multiple protocols, diverse name spaces, and a variety of authentication protocols.
NIST recognizes the problem with identity sprawl: “Often organizations do not have a complete inventory of their assets or a clear understanding of the criticality of their data. They also do not fully understand the transactions that occur between subjects, resources, applications, and services.” (lines 234-236). A lack of central visibility and control over the organizational assets represents a significant hurdle for the IT team for every project–not to mention a major concern for security posture.
Identity Data Strategy is a Key Enabler Across Security, Experience, and Efficiency Projects
All those digital transformation and security initiatives? They expect a single authoritative identity source. A complete “score” of identity data for real-time decisioning (access management), user lifecycle administration (governance), and analysis (audit).
Or, in the words of NIST: “In complex architectures, a ZTA requires an identity data foundation that bridges legacy systems and cloud technologies, and that extends beyond legacy AD domains.” (lines 2431-2433).
Another roadblock? The difficulty of integrating different components that must work together in a ZTA: “Organizations may not understand what interoperability issues may be involved or what additional skills and training network administrators may require, and they lack the resources to develop a pilot or proof-of-concept implementation needed to inform a transition plan.” (lines 241-244).
Let’s illustrate these challenges with the Zero Trust Architecture.
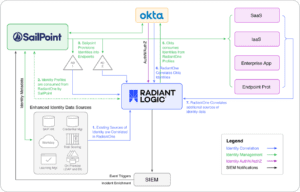
What is Radiant Logic doing in this diagram? Why aren’t the Identity Governance and Administration (IGA) and Identity and Access Management (IAM) solutions able to cover all the bases for Zero Trust-ing? Because identity unification–of which correlation is an important feature–is really its own category. Identity unification serves an indispensable purpose across the functions of IAM and IGA, and helps these components to work together better.
This core capability is required by a modern security architecture like Zero Trust–multiple services must be able to work in concert, operate off the same identity set, but they can’t do their jobs without the real-time access to rich identity data that identity unification provides.
Integrating identity needs to be a seamless, repeatable process. Whether for a merger or acquisition, for collaboration across entities or with partners, enabling stronger governance, or any other identity initiative, a unified source of identity accelerates and simplifies the project and shortens its timeline.
Identity Correlation Builds the Authoritative Source of Identity Data
Correlation creates the link that establishes a single identity for a same-user across sources–this enables Radiant to build complete, attribute-rich global profiles for users, for driving fine-grained access and turbo-boosting governance capabilities.
Often for complex infrastructures, advanced correlation is required for achieving identity unification. Above and beyond mere “aggregation” of identity data, and serving a different purpose than the integration of identity data that IGA provides, unification is the whole enchilada of integration.
NIST validates the requirement for unification in its implementation and explains how this unified identity foundation supports the other ZTA components of IAM and IGA: “Radiant Logic stores, normalizes and correlates this aggregation of information and extended attributes and provides appropriate views of the information in response to queries. RadiantOne monitors each source of truth for identity and updates changes in near real-time to ensure that Okta is able to enforce access based on accurate data. SailPoint is responsible for governance of the identity data.” (lines 2388-2392).
Identity Data Must be Managed Well to Support ZTA
Strategic management of identity data is a key enabler for enhanced cybersecurity. Every other system in the ZTA’s success hinges on how well the identity data is managed and made accessible to those components. As stated in NIST’s guide, “How ICAM information is provisioned, distributed, updated, shared, correlated, governed, and used among ZTA components is fundamental to the operation of the ZTA.” (lines 2380-2381).
Every consuming or “upstream” application needs access to valid, trusted identity data. The trick is to manage and maintain this data well despite complexity; that’s where an Identity Data Fabric comes in.
Identity Data Fabric is the Right Approach to Making Identity Data Accessible
It’s worth noting that another emerging pattern in the IAM market is the fabric or mesh approach–the pendulum has swung away from over-centralizing and over-synchronizing identity into a single “master” data source. That model has proven unwieldy, inflexible, and not scalable, which is why we are seeing distributed identity architectures taking center stage.
In the context of identity data, a fabric architecture leverages identity federation to weave the necessary elements of identity data into a central source, while allowing management of identity to remain local to authoritative systems. An Identity Data Fabric bridges the various identity needs across platforms and protocols, and provides a seamless experience for users, administrators, and developers– for harnessing the value of identity data. This approach avoids centralizing into a rigid structure that can’t evolve to meet changing requirements, or scale to modern organizational demands–like cloud, multi-cloud, and hybrid deployments, fine-grained access models, and rapid change ingestion.
Attributes are the Fuel for Fine-Grained Access Control
Fine-grained access policies can only be enforced when policy engines are equipped with real-time access to trusted and complete identity data. Attributes like role, group memberships, risk scores, and so on, are the necessary fuel for making a ZTA operate.
Zero Trust is inheriting lessons from the Attribute-Based Access (ABAC) model, segmenting its architecture by different function components like the Policy Enforcement Point (PEP), Policy Decision Point (PDP), and Policy Information Point (PIP).
NIST’s lab positions Radiant as the PIP for its ZTA implementation for complex environments: “Radiant Logic acts as a PIP for the PDP as it responds to inquiries and provides identity information on demand in order for Okta to make near-real time access decisions.” (lines 2374-2376). Radiant enables ABAC principles by delivering the necessary identity data and attributes for enforcing attribute-driven policies.
What Makes a Good Unified Identity Data Source?
I’ll leave you with a handy checklist of the capabilities you’ll want in your toolkit for upleveling your organization’s strategy for identity data management–and of course, for implementing ZTA.
A solution that is capable of building a unified identity data source from distributed systems:
- Delivers correlated, attribute-rich global profiles of all users (enabling fine-grained access control)
- Has flexible data modeling capabilities and standards-based accessibility
- Scales and performs for runtime access, even with hundreds of millions of identities
- Ensures resiliency, high availability, and gives deployment options (vendor and platform neutral)
- Automates groups definition and membership across sources
- Connects legacy, on-prem, cloud, multi-cloud identity environments
- Synchronizes data in near real-time so data is always coherent, valid, and propagated where required
If you want to learn more about Radiant Logic’s role in NIST’s Cybersecurity Practice Guide for Zero Trust Architecture, check us out here, or let us show you how we can help with a demo.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.




