The Flow of Security and the Benefits of an Identity Data Fabric
- Lauren Selby
- June 6, 2022
- Cybersecurity
- 4 MIN READ

Continuing our informal series on the centrality of (reliable and valid) identity data to an organization’s security strategy, we are looking at the “flow” of security through its four key “A” phases of authentication, authorization, administration, and audit.
The ability to fluidly extend access to digital services is crucial to business operations in many ways—workforce productivity, customer experience, mergers and partnerships… the list is pretty much infinite. The challenge is that managing and securing that access is increasingly complicated and difficult in a world where cyber attacks are seemingly continuous and continuously evolving, carried out by sophisticated bad actors, and very costly when successful. Building resilience and oversight into the access system is paramount. Constant vigilance doesn’t come cheap–your cybersecurity team needs a lot of tools to fend off these attempts. So how can you both: stop attacks, reduce resource costs and maybe even further your ROI all in one?
In their report on the topic, “The Flow of Security: Efficiency Relies on Identity Data,” Aite Novarica Group found that the “benefits of the flow of security start with and continually depend on the quality of identity data.”
The Flow of Security: Identity Data is the Source
Are you able to uniquely identify users with confidence? Automatically? Across multiple systems? And deliver that unique user’s entire breadth of information (or on the flip side, only a small subset of that user’s data) to consuming applications? That’s the foundation on which all good access decisions can be made.
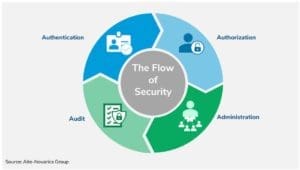
First thing’s first, let’s review these four A’s in detail. Let’s establish and verify who or what this account represents (in the authentication step). From there, we need access to complete, up-to-date information about that user (like their role, their group memberships for example) to enforce authorization—what are they allowed to do? Administration is the process by which all of this is made possible—the overall system for setting up user access according to specified rules and policies, shuttling identities through their lifecycle stages (creation, provisioning, updates, deletion), and all the attendant activities. The audit stage investigates whether the system is working properly—and from there, improvements can and should be made.
The “flow” is not only about having rock-solid security posture (which of course will save the organization the costs associated with a breach), but also managing identity data and security efficiently to avoid other unnecessary expenses—the IT effort, helpdesk hours, and wasted time for workforce that an enterprise incurs when access can’t be delivered seamlessly.
A process for continual improvement of both security and operational efficiency starts at the data layer: when management of identity data is optimized, every process that relies on that data benefits. The report puts it more directly:
“It is pointless to improve, say, a cloud access control broker or endpoint protection software if the organization plays loosey-goosey with identity and authentication. Investing in super-efficient administration software or high end-network monitoring will be a waste of money if organizations don’t first unify and streamline identity data.”
Valid Decisions are Built on Quality Identity Data
The trouble is, complex and large organizations have equally complex and difficult to manage identity infrastructures—there’s an ocean of information available but it’s disorganized, disjointed, not easy to direct. So even that first step of gaining visibility into identity isn’t easy. Assurance that identity data is valid—accurate, up to date, sourced from the authoritative system and so on—is not guaranteed due to the challenges inherent with identity sprawl.
But—good news alert—there is a method for turning that wealth of information into something functional for the organization: identity unification. That’s where an Identity Data Fabric comes in, weaving together siloed sources of identity data into a universally accessible resource—so all steps on the “flow of security” are supported by valid, rich identity information. As noted in the report:
“Security controls, administrative procedures, and event logs are only as reliable as the identity and authentication of users and systems. Therefore, unifying identity data and managing it with excellence will ensure the benefits and savings of the flow of security.”
Security Benefits of an Identity Data Fabric
Identity integration is often the hidden “project within a project” for extending access and deploying new solutions. Our customers often find out midway through an initiative that a lack of interoperability will delay their projects for months. Meanwhile, security gaps remain open, access is not granted appropriately, and money is being wasted. But, with an identity data foundation that ensures data accessibility in place, “… organizations can reap several benefits: efficient and effective buying decisions, excellent security processes and controls, resilient security posture, and moderate expenses.”
As found in the report, the benefits of an Identity Data Fabric follow four themes: resilience and oversight, end-user productivity, revenue growth, and extending business service.
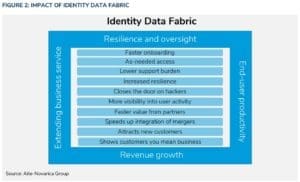
This is why having unified, good-quality identity data is so foundational for security—everything “upstream” relies on its accuracy and accessibility. The report makes it clear:
“Any improvement in the quality and management of identity data enhances all security investments.”
Even something simple like stronger authentication makes a huge difference. According to the report, “Strong multifactor authentication—sometimes as simple as using an app on a phone to validate a login request—reduces the likelihood of phishing by 70% to 90%.” But of course, that’s IF you can add MFA to all your applications, including legacy applications. An Identity Data Fabric ensures you can extend best IAM practices to every application, even non-standard ones that don’t support modern protocols.
Why does the Identity Data Fabric approach work while other solutions that try to completely centralize identity data fail? Because it lets local systems manage identity the way they are meant to, while intelligently pulling in what is needed for use at the global, abstracted layer: “Bringing all identity data into one centralized system for better management is not practical given the countless applications, formats, protocols, programs, and geographies in play. However, virtualization can unify identity without centralizing it.”
All security decisions stem from identity, so identity data needs to be complete, valid, and available to security enforcement engines. Evolving the practice of security within your organization should begin with optimizing identity data management to see the maximum benefit of investment in security tools.
Read the complete report here to learn more about helping your organization to “go with the flow” of security.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.




