The Relationship Between IAM and IT Risk Management
- The Radiant Team
- August 3, 2022
- Cybersecurity
- 4 MIN READ

It’s no secret that today’s IT landscape is under attack. The shift to the cloud, remote work and the IoT are quickly complicating the identity access management (IAM) landscape and expanding the attack surface. This is especially true with organizations working in hybrid IT environments.
These hybrid environments have created identity sprawl: the out-of-control increase of disconnected identity data throughout an enterprise. Identity sprawl makes enforcing security, governance, and compliance policies nearly impossible, opening organizations up to significant security risks.
How can organizations manage these risks more effectively? By integrating identity data into a single resource that can drive an effective IAM and identity governance and administration (IGA) infrastructure.
In a recent report, TechVision Research said it best, “protection of information assets is necessary to establish and maintain trust between the enterprise and its customers, partners and oversight bodies, maintain compliance with the law, and protect the reputation of the organizations.”
Want to learn more? Read the TechVision Research report, Architecting and Managing Hybrid and Cloud-Based Identity Services.
Two Key Components of IT Risk Management
Effective IT risk management includes a wide range of policies and procedures. However, two key components of any IT risk management strategy include IAM and IGA. These are interlocking components of any security and identity system that must be used in conjunction to avoid dangerous security risks.
1. IAM: Identity & Access Management
At a high level, IAM refers to the process of ensuring the right people are granted access to the right resources. Identities are confirmed by authenticating credentials found in a stored entry for them (their account) and then access is granted based on the specified level of entitlement.
There are various components within access management, including web access management and single sign-on (SSO) as well as federated identity management. It all comes back to authentication and authorization which form the core operations of extending access appropriately.
2. IGA: Identity Governance & Administration
A comprehensive identity system will go beyond IAM to include identity governance and administration (IGA). IAM encompasses everything to do with establishing access privileges, while IGA poses a few questions:
- Is the IAM system working appropriately?
- What systems can we implement to ensure our IAM system has access to the most comprehensive identity data to make the best security decisions?
- How can we prove our IAM systems meet established security standards and best practices?
In identity governance, several components are required, including centralized audits, logging and monitoring, access certification, and reporting. And in identity administration, methods include user self-service, delegated administration, automation workflows, and role definition.
When IAM and IGA are working as they should, companies can strengthen security by quickly identifying and mitigating inappropriate access or additional vulnerabilities. They can also ensure compliance and improve the overall experience for system users.
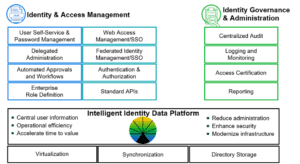
Both Components Require Access to Consolidated Identity Data
As mentioned above, both IAM and IGA are critical for effective IT risk management. Unfortunately, in today’s hybrid environment, it’s common for identity data to be spread across multiple silos. These silos are the enemy of IAM and IGA.
For example, a critical part of IGA is auditing user roles and their access to ensure users have access to the things they should. Nothing more, nothing less. This goal is often summarized as “least privilege access.”
When identity data is spread across these silos, getting an up-to-date glimpse of identity and access is impossible. The result? Security holes, failed audits, a lack of compliance…the list goes on.
IT teams need real-time data about existing users across all data silos to determine and enforce access controls. But this often requires customized solutions that are extremely complex and costly. And most IGA solutions don’t provide a comprehensive view of permission groups and roles across all resources—for use for real-time access.
The solution can be found with the RadiantOne Intelligent Identity Data Platform.
Transform Your Identity Data With RadiantOne
With the RadiantOne platform, you can easily construct a flexible Identity Data Fabric, a reusable source of identity truth.
RadiantOne gives you access to a flexible, inoperable layer that consolidates distributed identity data. Acting as a virtualization and abstraction layer, it unifies identity silos into a single central point for all applications.
Plus, the global synchronization is bi-directional and in real-time, enabling you to propagate and update identities across legacy and cloud-based systems.
With full and instant visibility into your identity data, you can reduce identity gaps and better implement IAM and IGA systems that improve risk management for your entire organization.
Learn More About IAM & IT Risk Management With Radiant Logic
Effective IT risk management requires IAM and IGA. However, successful IAM and IGA are not possible without access to unified identity data. RadiantOne provides you with an Identity Data Fabric so you can turn your identity into a single source of truth for any security initiative.
To learn more, check out our webinar, How to Thrive in a Hybrid World: Managing Identities for the Here and Now. Or, if you have questions or want to test drive RadiantOne in your organization, reach out to us today.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.



