Identity Data is the Key to Your Security Infrastructure
- The Radiant Team
- June 29, 2022
- Identity Data Fabric
- 6 MIN READ

As identity sprawl accelerates and identity information is spread across a complex web of legacy, hybrid, and multi-cloud systems, your organization is unintentionally putting itself at greater risk. The lack of visibility across all these systems creates security gaps—offering more opportunities for misuse or negligence by employees, and opening the door for cybercriminals to take advantage.
According to one survey of security professionals, each instance of credential theft or misuse is prohibitively expensive. Employees who misuse credentials cost companies an average of $307,111, but the cost nearly triples to $871,686 if it involves an imposter or thief who steals credentials. Companies today simply cannot afford to spend these millions annually on investigation and remediation of credential incidents.
Many companies rely on a combination of technology and policies to mitigate their security risks. End users are often tasked with managing their various access information because they use many different systems–putting the onus on them to manage their own security, which is far from best practice. IT teams are tasked with deploying the right combination of technologies to manage identity and keep things secure—in an increasingly complex and difficult to manage environment.
When an organization finds itself with a mix of data sources (home grown or legacy,
on-prem, in the clouds, and so on), the identity infrastructure becomes difficult to manage efficiently, and security becomes exponentially more challenging. How can companies ensure that only authorized and approved users access systems and resources without putting all the responsibility on employees?
Zero Trust is the newest approach to the challenge of securely connecting users to IT resources. Let’s get into it: keep reading to learn what that means, and how to implement it, even with a complex identity environment.
Using Identity Data to Enforce Security Policies
If you’re a cybersecurity professional, you might wonder how you can authenticate and authorize users based on information sourced from multiple stores—to get finer-grained access control. When the identity data relevant to each user is spread across the infrastructure, there’s no one spot that a policy enforcement point can connect to,
to assess a complete set of information and enforce access policies. This is a common challenge when the organization has identity stored in different formats, accessible through different protocols, and lacks an overarching unified list of users. Most large companies have a decentralized environment so it’s nearly impossible to manage access centrally
and granularly.
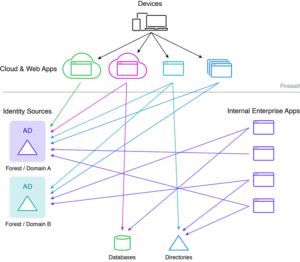
All this complexity is difficult for IT and security teams to manage. An approach to simplify this complexity moves the responsibility for the security and management of identities to an Identity Data Fabric which can intelligently gather and manage the multiple identity sources required to extend access for users.
An Identity Data Fabric approach is the key to enabling a Zero Trust framework, making it easier and efficient to manage identity data across multiple sources through unified identity data. Let’s take a closer look at Zero Trust and how it can unlock better cybersecurity.
What is Zero Trust?
Zero Trust is an “architectural state of mind,” as Paul Simmonds, fellow analyst at KuppingerCole, explained at the KuppingerCole Cyber Security Leadership Summit.
It’s a security framework deployed at the enterprise level that removes implicit trust and enforces user and device authentication throughout the entire network.
In the past, companies have been too trusting of users and devices by default. “Traditional corporate networks typically give too many people too much access for no particular purpose,” the creator of the Zero Trust strategy told Computer Weekly. This led to unintentional abuse by internal users and made it easier for criminals to take advantage of the situations, with criminal insider threats now making up 23% of all security incidents, according to one survey of cybersecurity professionals.
The Benefits of Zero Trust
The Zero Trust security model means that no user, even if they are on the network, is trusted by default, as they could be compromised.
When implemented, Zero Trust frameworks:
- Require identity and device authentication multiple times throughout the network so you can implement extremely granular security models
- Limit the number of opportunities for criminals or bad actors to gain access to secure content by restricting the parties with privileged access to each segment of a network, device, machine, and information
- Scale easily for today’s complex IT infrastructure models, including on-prem, cloud, and hybrid models, so every company can increase security
- Reduce the responsibility of users to maintain their profiles because it can be seamlessly combined with other security measures behind-the-scenes
While Zero Trust can enhance your organization’s cybersecurity, such an architecture requires access to the richest possible set of identity attributes. But gathering the needed identity data has long been a major pain point for complex organizations with years of identity investments and no small amount of identity sprawl.
An Identity Data Fabric can incorporate decentralized identity data because it’s built to unify identity across heterogeneous systems. With an Identity Data Fabric, it’s easy to incorporate your disparate identity data and update your security posture in a scalable, manageable, and secure way. Here are three ways it helps you leverage your identity data to drive better cybersecurity.
1. Create a Common Identity Data Model
Before: User profile attributes are spread across multiple sources, making it inefficient or impossible to create a single source of identity truth. Users are described differently in each source and have duplicate info stored in each. Plus, there’s no efficient way to map or align the data.
After: An Identity Data Fabric unifies identity data to create a complete global profile no matter the number of sources. Security teams can use the common identity to create policies that enforce more appropriate access and maintain them more efficiently no matter how often the data sources change.
2. Enable Access Easily Across Diverse Data Stores
Before: Identity data sources use different identification and credential-checking mechanisms, making it challenging for application and security teams to navigate when building access systems. It’s difficult to efficiently authenticate users because there are too many protocols and schema elements to handle, given that each user may have profiles across multiple sources, creating unnecessary work for IT teams when trying to extend access.
After: The Identity Data Fabric enables a single location for applications to go to for authentication and profile information that’s integrated with each store in the identity environment—without extra coding or advanced technical work. It offers a more flexible way to integrate identity data into a common security model.
3. Create Granular Security Profiles More Efficiently
Before: Security teams have trouble managing existing and potential group members as this data is spread across multiple sources, and can often be out of sync, not up-to-date, or inaccessible. Users are often assigned generic, high-level profiles based on incomplete information, again leaving security gaps that can be exploited.
After: Identity data, and groups data, can be integrated from multiple sources easily and efficiently with an Identity Data Fabric, offering more opportunities for you to categorize and group users in detailed and flexible profiles—easily.
The Smart Way to Integrate Identity Data Into Your Security Strategy
Think it costs too much to integrate identity data into your security strategy? Think again. Dealing with a data breach could cost your company anywhere from $4.58 million to $11.45 million. If that’s not enough, consider Gartner’s forecast that by next year, 80% of the new digital business applications opened to ecosystem partners will be accessed through Zero Trust Network Access (ZTNA), putting the pressure on organizations to prep their infrastructures for ZTNA use.
Security approaches have evolved today, as have the tools and technology used to support them, and an Identity Data Fabric accelerates adoption and modernization of all these identity-secured solutions. Radiant Logic can help you integrate all your identity sources into a more comprehensive security strategy—in fact, we’re the unified identity foundation of the Zero Trust model. We’ve got the expertise and tools that can start you on a more modern and sustainable security strategy.
An Identity Data Fabric can radically simplify management of your complex environment—and enable quicker adoption of best security practices. Contact us today to learn more about how RadiantOne can help you accelerate implementation of your Zero Trust Architecture.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.



