Migrating to Data-Centric ISPM
- Simon Moffatt
- June 16, 2025
- Identity Security Posture Management
- 5 MIN READ

This is the second in a three-part series of articles looking at the critical need to take a data-centric approach to identity. The first article conveyed why identity and access management in general is rapidly becoming a “big data” problem – and what that means and what benefits can be gained by taking such an approach.
In this article, we will apply our data-centric approach and understanding to delivering identity security posture management (ISPM).
The Rise of ISPM
- IGA in Distress
- ISPM as Evolution
- Continuous Compliance
It is important to define some constraints and capabilities surrounding ISPM and how this relates to both existing IAM infrastructure and to IGA.
ISPM focuses on the preventative and pre-breach control set. This means that it is important to consider that the controls being applied to IAM are being done on the data layer – which often focuses upon identity assurance, data hygiene and permissions life cycle management.
These controls can make a material difference as they pertain to risk impact and things like blast radius.
The cousin to ISPM in recent years is identity threat detection and response (ITDR). While intricately related – they are both focused on end-to-end identity, identity risk reduction and holistic protection – ITDR is often more focused on detection and post-breach, using response and controls that often influence in-flight attacks before they are completed. The remediation options available to ITDR and ISPM are often different, too.
ISPM has emerged in the past 3 years as both an extension and potentially an alternative design pattern to the traditional identity governance and administration (IGA) functions that emerged in the early 2000s. On the back of regulation such as Sarbanes Oxley and the Gramm Leach Bliley act, the US and more recently global financial institutions look to document and automate the “Who has access to what?” question. However, many IGA programs ended up in distress.
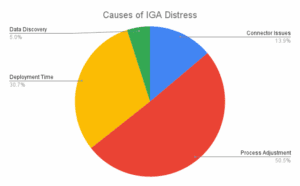
Source: The Cyber Hut Community Poll, April 2024, n=65
The causes are likely to vary depending on project size, sector and requirements, but some consistencies do emerge. Slow deployments, poor connectivity to integrated systems and costly and complex requirements to alter existing business processes all contribute to IGA capabilities that cover only a subset of systems.
The movement to a more continuous compliance initiative – one that places less emphasis on time consuming periodic reviews – sees ISPM aiming to leverage existing and evolving best practices around data hygiene with the application of both static and dynamic controls.
The benefits increase as more systems become part of the strategy – whether they be downstream managed applications or orthogonal systems that can provide information that helps deliver more context and insight.
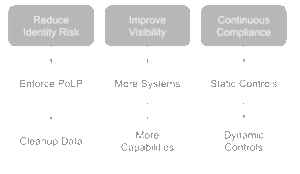
These economies of scale not only help deliver value by improving identity hygiene, access management and permissions clean-up for more systems, but they also help deliver analytics and insights. These insights are likely to support different stakeholders across the business in their pursuit of productivity improvements, faster application and identity onboarding, risk reduction and security improvements.
Improving with a Data-Centric View
- Data Fabric
- Insights for Pre-Breach
- Prevention as a Strategy
As we start to imagine a more data-centric approach to both IGA improvements and a strategic ISPM capability, we immediately begin to see both data sources and data consumers across our IAM landscape. As discussed in the first article in this series, a connected data fabric provides a bi-directional set of touch points that supports a conjoined and multiplying effect with respect to understanding how our identities are created, updated, used and managed. Identities (for both humans and non-humans) do not exist in a vacuum and are tightly coupled to business process and task completion.
However, numerous natural blind spots often exist within this life cycle in many organizations today. For example, this could include a lack of context during access requests, insufficient clarity during access reviews, or uncertainty when removing excessive permissions. Individually, these concerns are significant, but they often result in a cascading set of issues, as downstream systems and reactive detective controls are frequently built on false security assumptions. These false assumptions are implicitly built into relying on party systems, detective controls, and monitoring systems.

For example, assuming all identities have originated from an authoritative source often removes the secondary validation that helps identify ghost, orphaned, shared and redundant accounts. Downstream systems do not always provide ways of analyzing and questioning permission associations – they are more focused on whether a permission is present against an account in an access control entry. How that permission got there is assumed to be accurate. There is an assumption that removals and changes upstream are to be “automagically” relayed to a host of downstream systems. This is rarely the case.
These false assumptions and resulting failings in security posture are just some examples of the blind spots that are manifesting on the IAM life cycle management plane. Informed decision making is now possible by leveraging existing data sources across the technology landscape. This data-centric approach can help move organizations to a pre-breach way of reducing identity risk.
While detective, behavioral, and post-breach (and ideally, real-time breach) capabilities are critical, they must be grounded in strong, reliable identity data.
Getting Started
- Architecture and Concepts
- Start Small
- Process and Metrics
Delivering a data-centric IAM framework is a journey. While that may sound like a technological cliché, it is important to realize the factors involved in delivering success here. IAM is gaining in significance from being an operational and tactical component (which is often reactionary) to a strategic fulcrum that delivers productivity, security and revenue-generating opportunities. To that end, people, processes and technology must all change – and often that change will come at different times.
It is important to deliver each component of this journey in a way that aligns with the business’s current state and needs. This means that processes, workflows, job-specific tasks and ways of working have evolved over a considerable period of time and are inherently optimized based on effort, skill, and knowledge.
The IAM data foundation must integrate with these factors initially without change. Asking organizations to immediately alter onboarding or application access functions will simply inhibit adoption. Over time, those processes can be altered and optimized once managed within the system.
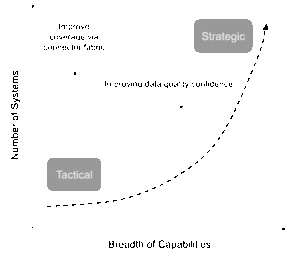
The journey for adoption will cover two main aspects: systems coverage and maturity, but also capability maturity. The integration of more systems is crucial – with some of those systems not having an IAM-centric background such as ISTM or CMDB.
Secondarily, the maturity of data-centric capabilities in these systems will also grow over time – from an initial reading and correlation of data sources to concepts like predictive analytics and human-in-the-loop, guided clean-up and remediation. The rise of AI is rapid and ever-changing, and organizations are quickly learning how to consume and leverage this new autonomous way of working through agentic AI and RAG-based querying. However, it still takes time to alter governance, operations, and accountability frameworks.
As with any journey through change, it is also important to quickly and clearly communicate success and metrics to a range of audiences. This will include non-technical stakeholders focused on improving productivity, reducing costs, and enhancing collaboration, as well as those interested in metrics related to risk reduction, connectivity, and overall performance.
The final article in this series will look at best practices and critical capabilities needed to succeed in this area.
Learn More
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.




