
Resources
- -
- Solutions
- RadiantOne
- Why Radiant Logic
- Company
- Support
- Resources
© 2026 Radiant Logic, Inc. All Rights Reserved. | Privacy Policy

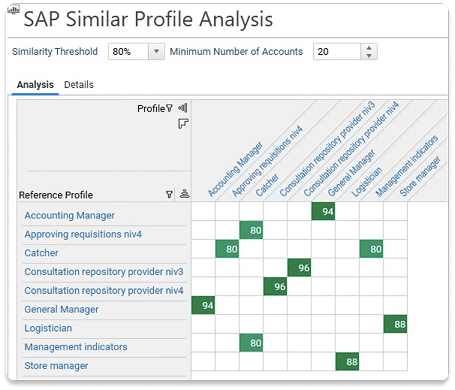
Role mining provides visibility into existing access patterns and translates them into manageable, business-aligned roles.
This reduces the chance of excessive entitlements, helps enforce least privilege, and creates a clear structure for demonstrating compliance to auditors. By turning messy entitlement data into validated role catalogs, organizations can strengthen security and simplify certification processes because it’s far easier to review and certify a well-defined role than hundreds of granular entitlements.

Organizations often lack insights into who ought to have access and why, making Role-Based Access Control (RBAC), which is considered an industry best-practice, tough to tackle. Associated difficulties include:
Radiant Logic addresses the limitations of IAM/IGA solutions by reflecting the business context associated with the role(s).
Role mining helps organizations analyze existing access patterns to propose business roles. When combined with governance review and business validation, it can reduce the risk of over-privileged access and streamline rights assignments.
Radiant Logic offers the three keys to successfully deploying role mining projects:
The solution is highly visual, efficient and fun! Useful information is immediately visible, allowing you to clean up and identify trends.
See the ways role mining can simplify access rights management, protection, and compliance.
Experience the Radiant Logic Platform and methodology with a personalized, hands-on demo.
© 2026 Radiant Logic, Inc. All Rights Reserved. | Privacy Policy